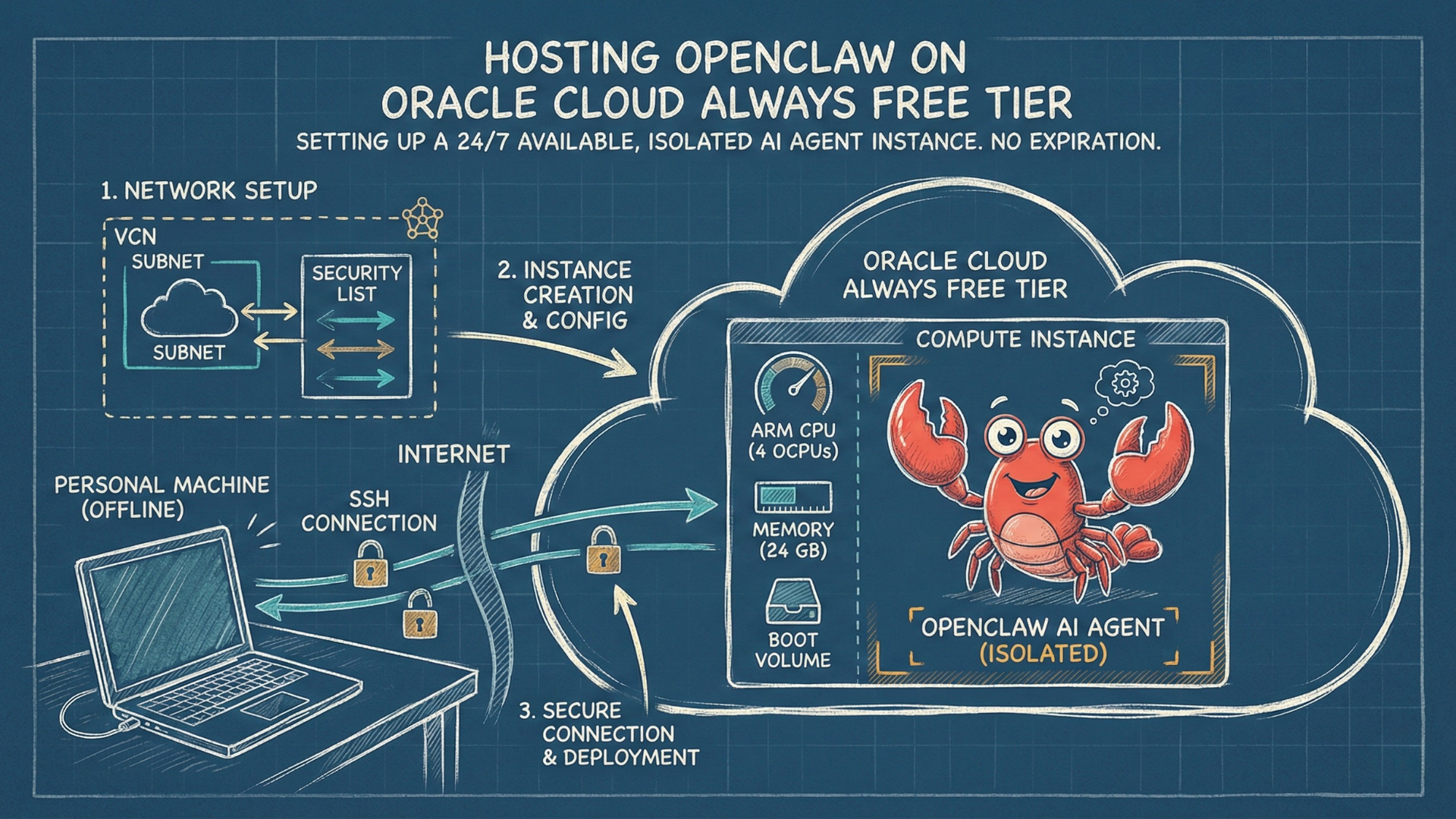
If you want to run OpenClaw — currently the most viral personal assistant AI agent — you need somewhere to host it. Running it on your personal machine faces two main challenges: it can’t stay on 24/7, and moreover, there have been many security concerns over running it directly on your personal infrastructure.
So you might want to check out cloud-based free hosting options, but most of them are limited. AWS’s free tier gives you a t2.micro with 1GB of RAM but only for 12 months. Moreover, OpenClaw doc listed 512MB - 1GB as minimum RAM size, but recommended 2GB. Pulumi’s deployment guide explicitly warns that 1GB instances are insufficient for OpenClaw. Google Cloud’s always-free e2-micro also offers 1GB of RAM. Heroku eliminated their free tier in 2022. Railway offers a credit-based model with 0.5GB of RAM per service on the free plan.
Oracle Cloud’s Always Free tier is a different class: 4 ARM CPU cores, 24GB of RAM, 200GB storage, no expiration. So you can even deploy multiple instances of the agent.
The tradeoff with Oracle Cloud is setup complexity — the console requires more configuration than a one-click deploy. That’s what this guide covers. By the end, you’ll have OpenClaw installed on an isolated cloud instance, ready to configure with your preferred AI model and messaging channel.
What you’ll need: An email address to sign up for an Oracle account, and a credit or debit card for verification only — you won’t be charged.
A note on security: hosting on an isolated cloud instance keeps the agent off your personal machine, but AI agents introduce security concerns beyond hosting. How you use it after setup can still expose you to various risks.
Now let’s get started.
Prefer video? Here’s the full walkthrough:
1. Create Your Oracle Cloud Account
Head to oracle.com/cloud/free and click “Start for free.” Fill in your details, verify your email, and set a password.
Oracle will ask for a credit card for identity verification only.
Choose Your Home Region
During signup, you’ll pick a home region. This is permanent — you cannot change it later. Choose a region geographically close to you, but be aware that popular regions often run out of free-tier capacity. Less congested alternatives may have more availability. Oracle documents capacity constraints in their Always Free availability documentation.
What you should see: The Oracle Cloud console dashboard. You’re logged in and ready.
2. Create a Compartment
Compartments are how Oracle Cloud organizes resources. Your account starts with a root compartment, but it’s good practice to create a dedicated one so your OpenClaw resources are isolated and easy to find.
- Click the hamburger menu (☰) → “Identity & Security” → “Compartments”
- Click “Create Compartment”
- Name:
Playground(or anything you like) - Description: e.g.,
OpenClaw testing environment - Parent Compartment: Leave as your root compartment
- Click “Create Compartment”
From here on, select Playground as the compartment whenever Oracle asks.
What you should see: Your new compartment listed under Identity → Compartments.
3. Create the Network (VCN) — Do This First!
This is a very important gotcha in this guide. Create your Virtual Cloud Network before you create your instance. If you skip this and try to create the network during instance setup, the public IP option will be grayed out — meaning you won’t be able to connect to your server via SSH. More details are available in Oracle’s public subnet documentation.
Run the VCN Wizard
- Click the hamburger menu (☰) in the top-left corner
- Go to “Networking”
- Click “Overview” tab if you are not there already
- Find “Create a VCN with internet connectivity” on the Networking overview page
- Click “Start VCN wizard”
Configure It
- VCN name:
openclaw-test(or anything you like) - Compartment: Select Playground (the one you just created)
- IPv4 CIDR blocks: If pre-populated, leave the defaults. If empty, enter
10.0.0.0/16for the VCN,10.0.0.0/24for the public subnet, and10.0.1.0/24for the private subnet - Review, then click “Create VCN”
Wait briefly for the “Virtual Cloud Network creation complete” message.
The wizard creates things you need in one shot: a public subnet, an internet gateway, proper routing, and security rules that allow SSH. Without the wizard, you’d have to configure each of these manually — and missing any one of them means no connectivity.
What you should see: Your VCN listed with status “Available” and 2 subnets (public and private).
4. Create the Compute Instance
Now that your network exists, you can create the server itself. Click the hamburger menu (☰), find “Instances” in the Pinned section, and click “Create instance.”
Name It
You can change the auto-generated name (something like instance-20260130-1556) to something memorable — e.g., instance-openclaw.
Choose the Image: Ubuntu 24.04 Minimal aarch64
Click “Edit” in the Image section, then “Change image.” Select:
Canonical Ubuntu 24.04 Minimal aarch64
With the following options:
- Ubuntu — Best community documentation for Node.js deployments
- 24.04 — Latest LTS, supported until April 2029
- Minimal — Smaller attack surface, faster boot, no unnecessary desktop packages
- aarch64 — Required for Oracle’s Always Free ARM allocation
Choose the Shape: 1 OCPU (Oracle CPU), 4GB RAM
After selecting the aarch64 image, Oracle may automatically switch your shape to VM.Standard.A1.Flex — that’s what we want. Click “Change shape” to configure it:
- Select “Ampere” (the ARM processor series)
- Check “VM.Standard.A1.Flex” — it shows an “Always Free-eligible” badge
- Click the small triangle (▶) next to VM.Standard.A1.Flex to expand the configuration. The OCPU and memory fields are hidden until you expand this section — an easy-to-miss UI detail
- Set Number of OCPUs: 1
- Set Amount of memory (GB): 4
- Click “Select shape”
Why not use the full 4 OCPU / 24GB? OpenClaw only needs about 2GB of RAM. Allocating 1 OCPU and 4GB gives you 2x the recommended memory while leaving 3 OCPUs and 20GB free for your other agents or projects. You can also resize later if needed.
Security Options
You’ll see toggles for “Shielded instance” and “Confidential computing.” Confidential Computing isn’t available on ARM shapes. Shielded instances harden low-level firmware security. It’s off by default, and you can choose whether to turn it on.
Configure Networking
Since you created the VCN first, this is straightforward:
- Primary network: Select “Select existing virtual cloud network”
- Virtual cloud network: Choose
openclaw-test - Subnet: Choose “Public Subnet-openclaw-test” — make sure it says “Public”
- Public IPv4 address: Toggle ON — “Automatically assign public IPv4 address”
The public IP toggle should be enabled (not grayed out) because you used the VCN Wizard. If it’s still grayed out, you could have selected the private subnet by mistake.
Add SSH Keys
SSH keys let you connect securely to your server. At the bottom of the Networking section:
Option A — Let Oracle generate keys (easier):
- Select “Generate a key pair for me”
- Click “Save private key” — downloads a
.keyfile - Click “Save public key” — downloads a
.pubfile - Store these safely. You cannot recover them if lost.
Option B — Use your existing key (if you have one):
- Select “Upload public key files”
- Upload your
~/.ssh/id_rsa.pubor~/.ssh/id_ed25519.pub
Storage
Leave the defaults. The 46.6GB boot volume is more than enough for Ubuntu + Node.js + OpenClaw, and it’s covered by your 200GB free storage. Keep the “Use in-transit encryption” toggled on.
Create It
Click “Create” and wait a few minutes. The status will change from PROVISIONING to RUNNING.
If You Get “Out of Host Capacity”
This is common — it means Oracle’s free ARM capacity is exhausted in your region. Your best option is to upgrade to Pay-As-You-Go (Billing → Upgrade and Manage Payment). This unlocks a larger resource pool without automatically charging you — you still get Always Free resources, and you only pay if you exceed the free limits. You can set a budget alert at $1 or less for peace of mind. This workaround is documented in this YouTube tutorial. The upgrade confirmation can take several hours to arrive.
Avoid Instance Reclamation
Oracle may reclaim idle free instances if CPU usage stays very low over a 7-day period. An active OpenClaw daemon should generate enough activity to avoid this, but review Oracle’s Always Free reclamation policy if your instance ever disappears unexpectedly.
What you should see: Your instance listed with status “Running” and a public IP address displayed.
5. Connect via SSH
Find your instance’s public IP address on the instance details page (e.g., xxx.xxx.xxx.xxx).
If Oracle Generated Your Keys
# Move keys to your .ssh directory (if multiple .key files exist, use the specific filename)
mv ~/Downloads/ssh-key-*.key ~/.ssh/oracle-cloud.key
mv ~/Downloads/ssh-key-*.pub ~/.ssh/oracle-cloud.key.pub
# Set correct permissions (SSH requires this)
chmod 400 ~/.ssh/oracle-cloud.keyConnect
# With Oracle-generated key:
ssh -i ~/.ssh/oracle-cloud.key ubuntu@YOUR_PUBLIC_IP
# With your existing key:
ssh ubuntu@YOUR_PUBLIC_IPThe first connection asks you to verify the host fingerprint — type yes.
The username is ubuntu because that’s the default for Ubuntu images on Oracle Cloud. Oracle Linux uses opc.
SSH Troubleshooting
| Error | Cause | Fix |
|---|---|---|
| ”Connection refused” | Instance still booting | Wait 2-3 minutes |
| ”Permission denied (publickey)“ | Key permissions wrong | Run chmod 400 on your private key |
| ”Connection timed out” | Firewall blocking | Check Security List has port 22 open |
| ”No route to host” | Instance not running | Check instance state in console |
What you should see: A terminal prompt like ubuntu@instance-openclaw:~$. You’re in.
6. Install OpenClaw
You’re now SSH’d into your Oracle Cloud instance. Time to install OpenClaw.
Update the System First
sudo apt update && sudo apt upgrade -yRun the Install Script
One command handles everything — Node.js and OpenClaw together. From the OpenClaw Getting Started guide:
curl -fsSL https://openclaw.ai/install.sh | bashThe install script detects your OS, installs Node.js 22 via NodeSource if it’s not present, installs OpenClaw globally via npm, runs migrations, and starts the onboarding wizard.
You’ll likely see this warning midway through:
WARN PATH missing npm global bin dir: /home/ubuntu/.npm-global/binFix it now so openclaw works in future terminal sessions:
echo 'export PATH="/home/ubuntu/.npm-global/bin:$PATH"' >> ~/.bashrc
source ~/.bashrcVerify Installation
openclaw --version
node --version # Should show v22.x.xWhat you should see: Version numbers for both OpenClaw and Node.js. The installation is ready.
7. Configure and Go
The install script launches an onboarding wizard. Read the security warnings carefully, then select Continue Quick Start.
Choose a Model Provider
The wizard asks for a model provider. As an example, we’ll use OpenRouter — a unified API gateway that gives you access to many AI models, including free ones.
- Select OpenRouter as your provider
- Enter your OpenRouter API key (create one at openrouter.ai/keys)
- Select a default model — for testing, you can pick a free model, e.g., tng-r1t-chimera
Skip the Telegram bot and other channel options during onboarding — we’ll configure Telegram after testing the basics.
The wizard installs a background service so OpenClaw runs 24/7 and survives reboots.
Test It
At the end of the wizard, you will be prompted “How do you want to hatch your bot?” We can select “Hatch in TUI” and start talking.
Type a message and wait for a response. If you’re using a free model, you may sometimes see rate limit errors (HTTP 429) — this is normal. Free models have usage caps. Wait a moment and try again, or add credits and switch to a paid model for more usage quota.
What you should see: A response from the AI in the terminal chat. Your agent is alive and running in the cloud.
Connect a Telegram Channel
Now let’s configure a Telegram channel so you can talk to your agent from your phone. Run:
openclaw configure --section channelsSince we’re running on this machine, select Local config, then Telegram.
The wizard asks you to create a bot token. Open Telegram on your phone, search for @BotFather, and send /newbot. Follow the prompts to name your bot — you’ll receive a token. Paste it into the wizard and click Finished. For the DM policy, leave it on the default: pairing.
Configuration is done. Now you need to approve your own Telegram account. First, open Telegram and send any message to your new bot — this triggers a pairing request. Then back on the server:
openclaw pairing list telegramYou’ll see your Telegram username and a pairing code. Approve it:
openclaw pairing approve telegram <CODE>That’s it — send a message to your bot on Telegram and you should get a response.
Next Steps
From here, follow the OpenClaw documentation to:
- Connect additional messaging channels if needed
- Choose a higher-quality model for better responses
- Configure tools and extensions to give your agent more capabilities
8. Keeping It Secure
Choose AI Models. While the onboarding wizard supports many models, frontier models like the latest version of Claude Opus offer an advantage beyond capability—they are also safer and demonstrate more resilience against prompt injection attacks.
Stay Updated. Update OpenClaw frequently by re-running the install script:
curl -fsSL https://openclaw.bot/install.sh | bashKeep Audited. Run openclaw security audit to check your setup. The audit scans network exposure (gateway binding, authentication, token strength), inbound access policies (who can message your bot), tool blast radius (elevated tools combined with open rooms), file permissions on credential files, and extension allowlists. Add --deep for a live gateway probe, or --fix to automatically apply safe defaults — it tightens group policies to allowlist-only, re-enables log redaction, and corrects filesystem permissions.
Be careful with credentials and personal data. Anything you give your agent access to — email, calendars, files — becomes part of its attack surface. Treat the default configuration as a starting point, not a finished setup.
Going further. This guide gets you running with the simplest setup — SSH keys and Oracle’s Security Lists protecting a public IP. Note that the key Oracle generated for you does not enforce a passphrase — anyone who gets the file gets access. For longer-term self-hosting, consider adding a passphrase (ssh-keygen -p -f ~/.ssh/oracle-cloud.key) and storing it in your OS keychain (ssh-add --apple-use-keychain on Mac) so it’s encrypted at rest without losing automation, adding Tailscale so SSH is no longer exposed to the internet, and enabling automatic security updates to keep patches applied automatically. Each layer reduces your attack surface without adding much complexity.
For a deeper understanding of OpenClaw and AI agent security in general — from prompt injection to supply chain attacks to emergent agent behaviors — check out: The Magic Is Real. So Are the Risks — A Security Analysis of OpenClaw and the AI Agent Era.
Let the magic shine — but stay safe.